使用 Azure AD 配置应用程序访问控制
MATLAB® Production Server™ 管理员可以使用 Microsoft® Azure® AD 将所部署应用程序的访问权限限制为仅限特定用户或用户组。要启用应用程序访问控制,请咨询 Azure AD 管理员以配置 Azure AD 并指定访问控制策略。
在 Azure 门户中注册应用程序
要使用 Azure AD 进行应用程序访问控制,请在 Azure 门户中注册一个服务器应用程序和一个客户端应用程序。这些应用程序与您可能为仪表板访问控制注册的应用程序不同。这些应用程序与部署到 MATLAB Production Server 的应用程序或使用 MATLAB Production Server 客户端库编写的客户端应用程序无关。
注意
应用程序的注册流程由 Azure 决定,有可能发生变化。
在 Azure 中注册服务器应用程序
登录到 Azure 门户。
从 Azure Active Directory 中选择 App registrations 并点击 New registration。
在出现的窗格中,输入应用程序的名称(例如,
MATLAB Production Server App),然后选择 Register。在您注册的应用程序中,选择 Expose an API。
点击 Add a scope,然后输入应用程序的范围信息。点击 Add Scope。有关添加范围的详细信息,请参阅 Microsoft Azure 文档。下表列出了添加范围时需要输入的字段和值。
字段 值 Scope name 输入名称,例如
user_impersonation。Who can consent 选择 Admin and users。Admin consent display name 输入名称,例如
Access MATLAB Production Server App。Admin consent description 输入描述,例如
Allow the application to access MATLAB Production Server App on behalf of the signed-in user。User consent display name 输入名称,例如
Access MATLAB Production Server App。User consent description 输入描述,例如
Allow the application to access MATLAB Production Server App on behalf of the signed-in user。State 选择 Enabled。点击左侧导航窗格中的 Manifest。在显示的 JSON 中,将
groupMembershipClaims的值设置为"SecurityGroup"。点击 Save。
在 Azure 中注册客户端应用程序
在 Azure 门户中,注册一个客户端应用程序。客户端应用程序帮助向服务器发送请求的客户端生成访问令牌。您可以将客户端应用程序注册为本机 App 或 Web App。如果将客户端应用程序注册为本机 App,则用户必须使用用户名和密码登录才能生成访问令牌。如果将客户端应用程序注册为 Web App,则用户必须使用浏览器通过单点登录来生成访问令牌。
根据您的组织设置,注册客户端应用程序可能需要在 Azure 中具有更高的特权。
将客户端应用程序注册为本机客户端
登录到 Azure 门户。
从 Azure Active Directory 中选择 App registrations 并点击 New registration。
在打开的窗格中,输入应用程序的以下注册信息,然后点击 Register。
字段 值 Name 输入名称,例如
MATLAB Production Server Native Client。Redirect URI 选择 Public client/native (mobile & desktop)。点击左侧导航窗格中的 Manifest。在 JSON 中,将
allowPublicClient的值设置为true。点击 Save。点击 API permissions,然后点击 Add a permission。
在打开的窗格中,点击 APIs my organization uses。
搜索您之前注册的
MATLAB Production Server App服务器应用程序。在打开的窗格中,选择范围名称(例如,user_impersonation),然后点击 Add permissions。
将客户端应用程序注册为 Web 客户端
登录到 Azure 门户。
从 Azure Active Directory 中选择 App registrations 并点击 New registration。
在打开的窗格中,输入应用程序的以下注册信息,然后点击 Register。
字段 值 名称 输入名称,例如
MATLAB Production Server Web Client。Redirect URI 选择 Web。输入客户端应用程序将使用的有效重定向 URI在左侧导航窗格中选择 Certificates & secrets。在 Client secrets 下,创建一个新的客户端机密,并保存机密的值。
点击 API permissions,然后点击 Add a permission 并选择 APIs my organization uses。
搜索您之前注册的
MATLAB Production Server App服务器应用程序。在打开的窗格中,选择范围名称,例如user_impersonation,然后点击 Add permissions。
配置身份提供方
在 Azure 门户中注册服务器应用程序和客户端应用程序后,在仪表板的 Application Access Control 选项卡中为 Azure AD 创建配置。点击 Create 并选择 Azure AD。
在 Azure 门户中,找到您组织的租户 ID 以及您之前注册的服务器应用程序的应用程序 ID。在 Create Identity Provider for Application Access Control 下的仪表板中输入租户 ID 和应用程序 ID。
登录到 Azure 门户。
从 Azure Active Directory 中选择 Properties。从 Directory (tenant) ID 复制值并将其粘贴到仪表板中的 Tenant ID 字段中。
从 Azure Active Directory 中选择 App registrations。选择用于 MATLAB Production Server 的应用程序,例如
MATLAB Production Server App。从 Application (client) ID 复制值并将其粘贴到仪表板中的 Server App ID 字段中。在仪表板中,点击 Create。如果服务器在 Windows® 虚拟机上运行,保存值可能需要长达 30 秒的时间。
指定访问控制策略规则
通过定义访问控制策略规则来指定特定用户组可以访问的应用程序。要定义规则,请点击仪表板 Application Access Control 选项卡中 Access Control Policy 下的 Add Rule。指定以下值。
| 字段 | 值 |
|---|---|
| Rule ID | 规则的名称 |
| 描述 | 规则描述 |
| Users | 在 Azure AD 中设置的允许访问所部署应用程序的用户名 |
| Groups | 在 Azure AD 组中设置的允许访问所部署应用程序的组的对象 ID |
| Applications | 指定用户和组可以访问的应用程序。 要选择所有应用程序,请选择 |
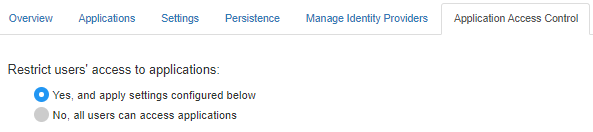
启用应用程序访问控制
配置身份提供方并指定访问控制策略规则后,您必须通过从仪表板中选择 Yes 选项来启用仪表板访问控制。
生成访问令牌
启用应用程序访问控制后,访问控制策略规则中指定的用户可以生成持有者访问令牌。如果注册的客户端应用是本机 App,请使用用户名和密码登录,或者集成 Windows 身份验证来生成访问令牌。如果注册的客户端应用程序是 Web App,请使用浏览器通过单点登录来生成访问令牌。您可以使用 Microsoft 身份验证平台库(Microsoft 支持的客户端库或者不同编程语言兼容的客户端库)来生成访问令牌。有关详细信息,请参阅 Microsoft 文档。当您使用 MATLAB Production Server RESTful API 向服务器发出请求时,请在 HTTP 授权标头中使用此访问令牌。此标头的格式为 Authorization:Bearer <access token>。