准备安装
Polyspace® Access™ 提供了一个 Web 浏览器界面,以便您可以审查托管在集中化数据库中的 Polyspace 分析结果。当您安装 Polyspace Access 时,会安装以下 App:
User Manager:根据公司的轻型目录访问协议 (LDAP) 或根据自定义的内部用户数据库对用户登录进行身份验证。App 向通过身份验证的用户颁发已签名的 JSON Web 令牌,并提供用于管理用户自定义数据库的用户界面。
Issue Tracker:管理 Polyspace Access 与 Bug 跟踪工具 (BTT) 软件之间的通信,并提供用于创建 BTT 工单的用户界面。
Polyspace Access:管理上传到 Polyspace Access 数据库的结果以及从该数据库导出的结果,并提供用于审查结果的用户 Web 界面。
Polyspace Access ETL (Extract-Transform-Load) 服务处理结果上传、结果下载,以及更新显示在用户 Web 界面中的数据等操作。
每个 App 都包含部署在 Docker 容器内的服务。还有一个单独的 Gateway 服务用来处理 Polyspace Access 与客户端计算机之间的通信。
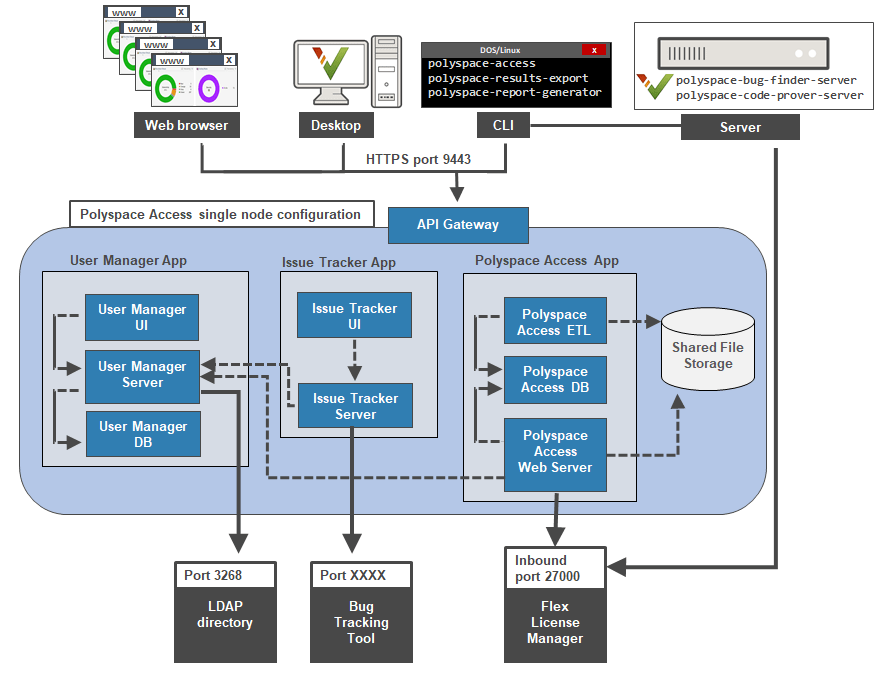
在开始安装前,请决定是否使用 HTTPS 协议以及如何配置用户身份验证和 Bug 跟踪工具集成。
提示
您可以使用 Kubernetes® 来部署 Polyspace Access。有关详细信息,请联系 MathWorks 技术支持。
您可以使用关系数据库服务 (RDS) 来托管 Polyspace Access 数据库。有关详细信息,请联系 MathWorks 技术支持。
常规前提条件
安装所需的软件并确保您的系统满足最低硬件要求。请参阅Polyspace Access 的系统要求。
验证您是否有足够的数据存储可用,使用的端口是否可用且未被防火墙阻止。请参阅存储和端口配置。
确认许可证管理器已安装且正在运行,并且许可证管理器选项文件包含您向其授予 Polyspace Access 使用权的用户。请参阅管理 Polyspace NNU 许可证。
为避免许可证文件操作出现任何潜在问题,每次升级 Polyspace Access 时都应考虑升级网络许可证管理器软件。请参阅更新网络许可证管理器软件。
如果您在 Windows Server® 2016 或 2019 上的 Linux® 虚拟机 (VM) 中安装 Polyspace Access,请创建并配置 Linux 虚拟机。请参阅使用 Hyper-V 创建 Linux 虚拟机。
如果您启用 HTTPS 来加密 Polyspace Access 与客户端计算机之间的通信,请从证书认证中心获取 SSL 私钥和签名证书,或者使用自签名证书。请参阅为 Polyspace Access 选择 HTTP 或 HTTPS 配置
如果您将 Polyspace Access 配置为使用 HTTPS 协议,则必须生成一个 Java® 密钥存储 (
JKS) 文件以启用 Polyspace Access 与 Polyspace 桌面端界面(或polyspace-results-export和polyspace-report-generator二进制文件)之间的通信。请参阅生成客户端密钥库。确保 Docker 网络与现有网络不存在冲突。有关 Docker 网络的详细信息,请参阅网络概述。
要检查您的 Docker 网络是否与现有网络冲突,请运行以下命令:
并确保docker network inspectnetworkNameIPAM.Config节点中列出的 IP 范围未被其他服务使用。您可能需要联系您的网络管理员来确定 IP 范围是否被其他服务使用。要查找
networkName,请使用docker network ls命令。如果此命令返回了多个网络,请检查所有桥网络(请参阅输出中的DRIVER列)。请创建一个网络并指定子网和网关,以避免与现有网络冲突。请参阅创建 docker 网络。要使用新网络,在启动
--network-name二进制文件时请使用admin-docker-agent选项。
使用 User Manager 的前提条件
进行 User Manager 配置需要生成一个 SSL 私钥文件。请参阅配置 User Manager。此私钥必须不同于您用于 HTTPS 配置的私钥。
如果您使用公司 LDAP 对用户登录进行身份验证,请联系您的 LDAP 管理员以:
获取组织使用的 LDAP URL 和 LDAP 库。
获取 LDAP 登录凭据(如果对 LDAP 服务器的访问受密码保护)。
找出可用于从 LDAP 数据库中检索特定用户子集的 LDAP 搜索过滤器。请参阅 LDAP 过滤器。
如果使用基于 SSL 配置的 LDAP 服务器 (LDAPS),则必须将 LDAPS SSL 证书添加到用于 Polyspace Access 的证书信任存储文件中。请参阅为基于 SSL 的 LDAP 配置 User Manager。
Issue Tracker 的前提条件
进行 Issue Tracker 配置需要使用您用于连接到 BTT 界面的 URL。
如果您使用 Jira 软件与 OAuth 身份验证方法,则必须先在 Jira 中创建一个应用程序链接。请参阅此页面上的第一个步骤。
如果您使用 Redmine BTT,请联系您的 Redmine 管理员获取 Redmine API 密钥。
如果您使用通过 HTTPS 配置的 BTT,则必须将 BTT SSL 证书添加到用于 Polyspace Access 的证书信任存储文件中。请参阅添加使用 HTTPS 配置的 BTT 实例。
WSL 上的 Polyspace Access 支持
不支持在适用于 Linux (WSL) 的 Windows 子系统上安装 Polyspace Access。
WSL 是一项 Windows® 功能,使您能够从 Windows 在 Linux 文件系统上执行 Linux 命令行工具,同时使用比常规虚拟机 (VM) 更少的资源。虽然您可以使用 WSL 进行开发,但此功能缺少常规 Linux 操作系统的某些功能。请参阅我能否将 WSL 用于生产场景?
请注意,WSL2 提供了改进的性能,但依赖于虚拟化网络组件,并且在 OS 文件系统中表现不佳。以上两个问题都影响了 Polyspace Access 的性能。请参阅比较 WSL 版本。