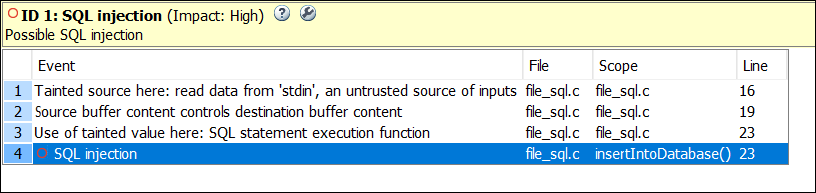
SQL injection
Data read from an untrusted source is used in the construction of an SQL query
Since R2023a
Description
This checker is deactivated in a default Polyspace® as You Code analysis. See Checkers Deactivated in Polyspace as You Code Analysis (Polyspace Access).
This defect occurs when data read from an untrusted source such as standard input is used in the construction of an SQL query.
This defect checker detects the flow of data from an untrusted source to a function that executes an SQL query (or prepares an SQL query to execute later). The checker flags functions from the following API-s:
MySQL C API – SQL query functions such as
mysql_query()andmysql_real_query().SQLite API – SQL query functions such as
sqlite3_exec()or SQL statement preparation functions such assqlite3_prepare()andsqlite3_prepare_v2().
Untrusted sources include strings read from the standard input stdin using the fread() or fgets() function or from files opened with fopen(). Note that unlike other Bug Finder checkers, this checker skips functions not called directly or indirectly from the main function (if there is a main).
Note that the defect checker is not available in the Polyspace user interface and is disabled even if you select the value all for the option Find defects (-checkers). For the issue to be detected, the checker must be enabled explicitly using the option -checkers SQL_INJECTION.
Risk
If you construct SQL queries from user inputs but use the inputs directly in the query construction without any sanitization, the queries are vulnerable to SQL injection. A malicious user can inject code masquerading as input, resulting in:
Bypassing of logic that secures part of the database.
Execution of malicious SQL queries or shell commands.
For instance, this SQL query, where the variables usernameitemName
SELECT * FROM items WHERE owner = 'userName' AND itemname = 'itemName';
john and anItem' OR 'a' =
'a, the query translates to:SELECT * FROM items WHERE owner = 'john' AND itemname = 'anItem' OR 'a' = 'a';
WHERE clause is always true. This allows the user to access the entire database even if they do not have the requisite permissions.Fix
Depending on the API you are using, follow these sanitization approaches to sanitize user inputs before using them in SQL queries. For instance:
MySQL C API – Escape values in the SQL query string using
mysql_real_escape_string()ormysql_real_escape_string_quote().SQLite API – Create parametrized queries using the functions
sqlite3_prepare_*()with parameters and then bind the parameters using the functionssqlite3_bind_*().
You can also write your own sanitization functions to validate or clean up the user input. For information on how to make the checker aware of custom sanitization functions, see the next section.
Extend Checker
You can extend this checker by specifying your own SQL statement execution and sanitization functions.
Suppose you want to specify that:
Function
sql_execexecutes an SQL statement or prepares an SQL statement for execution:int sql_exec (char*, /* SQL query */ sqlite3* , /* Database */ int (*callback)(void*,int,char**,char**), void*, char**);Suppose the
n_execFunction
sql_sanitizesanitizes the untrusted (tainted) data that is later used in an SQL statement.int sql_sanitize( char *, /* String to sanitize */ int); /* Length of string */Suppose the
n_sanitize
To make the SQL injection checker aware of these functions:
In a file with extension
.dl, add this code:If.include "models/interfaces/sql.dl" Sql.Basic.execution("sql_exec", $InParameterDeref(n_exec-1)). Sql.Basic.sanitizing("sql_sanitize", $OutParameterDeref(n_sanitize-1)).n_execn_sanitize.include "models/interfaces/sql.dl" Sql.Basic.execution("sql_exec", $InParameterDeref(0)). Sql.Basic.sanitizing("sql_sanitize", $OutParameterDeref(0)).Specify this file using the option
-code-behavior-specifications. For instance, if the file is namedsqlAdditionalFunctions.dl, use the analysis option:-code-behavior-specifications sqlAdditionalFunctions.dl
Examples
Result Information
| Group: Security |
| Language: C | C++ |
| Default: Off |
Command-Line Syntax:
SQL_INJECTION |
| Impact: High |
Version History
Introduced in R2023a
See Also
Topics
- Interpret Bug Finder Results in Polyspace Desktop User Interface
- Interpret Bug Finder Results in Polyspace Access Web Interface (Polyspace Access)
- Address Results in Polyspace User Interface Through Bug Fixes or Justifications
- Address Results in Polyspace Access Through Bug Fixes or Justifications (Polyspace Access)