Review and Fix Illegally Dereferenced Pointer Checks
This topic describes how to systematically review the results of an Illegally dereferenced pointer check in Polyspace® Code Prover™.
Follow one or more of these steps until you determine a fix for the Illegally
dereferenced pointer check. There are multiple ways to fix this check.
For a description of the check and code examples, see Illegally dereferenced pointer.
Sometimes, especially for an orange check, you can determine that the check does not represent a real error but a Polyspace assumption that is not true for your code. If you can use an analysis option to relax the assumption, rerun the verification using that option. Otherwise, you can add a comment and justification in your result or code.
For the general workflow that applies to all checks, see Interpret Code Prover Results in Polyspace Desktop User Interface or Interpret Code Prover Results in Polyspace Access Web Interface (Polyspace Access).
Step 1: Interpret Check Information
Place your cursor on the dereference operator.
Obtain the following information from the tooltip:
Whether the pointer can be
NULL.In the following example,
ptrcan beNULLwhen dereferenced.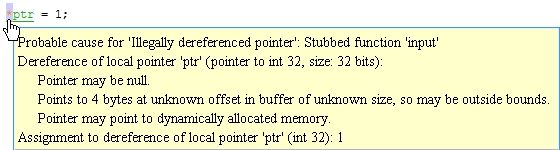
Possible fix: Dereference
ptronly if it is notNULL.if(ptr !=NULL) *ptr = 1; else /* Alternate action */Whether pointer points outside the allocated buffer. A pointer points outside the allocated buffer when the sum of pointer size and offset is greater than buffer size.
In the following example, the offset size (4096 bytes) together with pointer size (4 bytes) is greater than the buffer size (4096 bytes). If the pointer points to an array:
The buffer size is the array size.
The offset is the difference between the beginning of the array and the current location of the pointer.
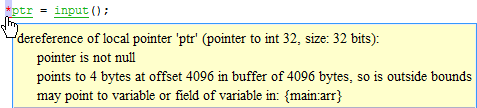
Possible fix: Investigate why the pointer points outside the allocated buffer.
Whether pointer can point outside the allocated buffer because buffer size is unknown.
In the following example, the buffer size is unknown.
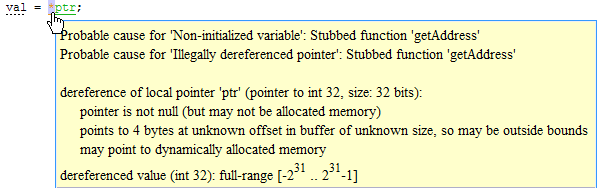
Possible fix: Investigate whether the pointer is assigned:
The return value of an undefined function.
The return value of a dynamic memory allocation function. Sometimes, Polyspace cannot determine the buffer size from the dynamic memory allocation.
Another pointer of a different type, for instance,
void*.
The probable root cause for illegal pointer dereference, if indicated in the tooltip.
In the following example, the software identifies a stubbed function,
getAddress, as probable cause.
Possible fix: To avoid the illegally dereferenced pointer, constrain the return value of
getAddressto provide design information that exists outside your code. For instance, you might specify thatgetAddressreturns a pointer to a 10-element array. For more information, see Code Prover Assumptions About Stubbed Functions.
Step 2: Determine Root Cause of Check
Select the check and note the information on the Result Details pane.
If the Result Details pane shows the sequence of instructions that lead to the check, select each instruction and trace back to the root cause.
If the Result Details pane shows the line number of probable cause for the check, in the Polyspace user interface, right-click the Source pane. Select Go To Line.
Otherwise, based on the nature of the error, use one of the following methods to find the root cause. You can perform the following steps in the Polyspace user interface only.
Error How to Find Root Cause Pointer can be NULL.Find an execution path where the pointer is assigned the value NULL or not assigned a definite address.
Right-click the pointer and select Search For All References.
Find each previous instance where the pointer is assigned an address.
For each instance, on the Source pane, place your cursor on the pointer. The tooltip indicates whether the pointer can be
NULL.Possible fix: If the pointer can be
NULL, place a check forNULLimmediately after the assignment.if(ptr==NULL) /* Error handling*/ else { . . }If the pointer is not
NULL, see if the assignment occurs only in a branch of a conditional statement. Investigate when that branch does not execute.Possible fix: Assign a valid address to the pointer in all branches of the conditional statement.
Pointer can point outside bounds allowed by the buffer. Find the size of the allocated buffer.
On the Search tab, enter the name of the variable that the pointer points to. You already have this name from the tooltip on the check.
Search for the variable definition. Typically, this is the first search result.
If the variable is an array, note the array size. If the variable is a structure, search for the structure type name on the Search tab and find the structure definition. Note the size of the structure field that the pointer points to.
Find out why the pointer points outside the allocated buffer.
Right-click the pointer and select Search For All References.
Identify any increment or decrement of the pointer. See if you intended to make the increment or decrement.
Possible fix: Remove unintended pointer arithmetic. To avoid pointer arithmetic that takes a pointer outside the allocated buffer, use a reference pointer to store its initial value. After every arithmetic operation on your pointer, compare it with the reference pointer to see if the difference is outside the allocated buffer.
Step 3: Look for Common Causes of Check
Look for common causes of the Illegally dereferenced pointer check.
If you use pointers for moving through an array, see if you can use an array index instead.
Use of pointer arithmetic navigating through an array causes violations of MISRA C™: 2023 rule 18.4. Use Polyspace Bug Finder™ to check for violations of this rule. See
MISRA C:2023 Rule 18.4.See if you use pointers for moving through the fields of a structure.
Polyspace does not allow the pointer to one field of a structure to point to another field. To allow this behavior, use the option
Enable pointer arithmetic across fields (-allow-ptr-arith-on-struct).See if you are dereferencing a pointer that points to a structure but does not have sufficient memory for all its fields. Such a pointer usually results from type-casting a pointer to a smaller structure.
Polyspace does not allow such dereference. To allow this behavior, use the option
Allow incomplete or partial allocation of structures (-size-in-bytes).If an orange check occurs in a function body, see if you are passing arrays of different sizes in different calls to the function.
See if one particular call causes the orange check. For a tutorial, see Identify Function Call with Run-Time Error.
See if you are performing a cast between two pointers of incompatible sizes.
Step 4: Trace Check to Polyspace Assumption
See if you can trace the orange check to a Polyspace assumption that occurs earlier in the code. If the assumption does not hold true in your case, add a comment or justification in your result or code. See Address Results in Polyspace User Interface Through Bug Fixes or Justifications or Address Results in Polyspace Access Through Bug Fixes or Justifications (Polyspace Access).
For instance, suppose that the pointer receives an address from an undefined function. Then:
Polyspace assumes that the function can return
NULL.Therefore, the pointer dereference is orange.
Polyspace also assumes a buffer size based on the type of the pointer.
If you increment the pointer, you exceed the allocated buffer. The pointer dereference that follows the increment is orange.
If you know that the function returns a non-
NULLvalue or if you know the true allocated buffer, add a comment and justification in your code describing why you did not change your code.
For more information, see Code Prover Analysis Assumptions.
Note
Before justifying an orange check, consider carefully whether you can improve your coding design.