Design a Deep Neural Network with Simulated Data to Detect WLAN Router Impersonation
This example shows how to design a radio frequency (RF) fingerprinting convolutional neural network (CNN) with simulated data. You train the CNN with simulated wireless local area network (WLAN) beacon frames from known and unknown routers for RF fingerprinting. You then compare the media access control (MAC) address of received signals and the RF fingerprint detected by the CNN to detect WLAN router impersonators.
For more information on how to test the designed neural network with signals captured from real Wi-Fi® routers, see the Test a Deep Neural Network with Captured Data to Detect WLAN Router Impersonation example.
Detect Router Impersonation Using RF Fingerprinting
Router impersonation is a form of attack on a WLAN network where a malicious agent tries to impersonate a legitimate router and trick network users to connect to it. Security identification solutions based on simple digital identifiers, such as MAC addresses, IP addresses, and SSID, are not effective in detecting such an attack. These identifiers can be easily spoofed. Therefore, a more secure solution uses other information, such as the RF signature of the radio link, in addition to these simple digital identifiers.
A wireless transmitter-receiver pair creates a unique RF signature at the receiver that is a combination of the channel and RF impairments. RF Fingerprinting is the process of distinguishing transmitting radios in a shared spectrum through these signatures. In [1], authors designed a deep learning (DL) network that consumes raw baseband in-phase/quadrature (IQ) samples and identifies the transmitting radio. The network can identify the transmitting radios if the RF impairments are dominant or the channel profile stays constant during the operation time. Most WLAN networks have fixed routers that create a static channel profile when the receiver location is also fixed. In such a scenario, the deep learning network can identify router impersonators by comparing the received signal's RF fingerprint and MAC address pair to that of the known routers.
This example simulates a WLAN system with several fixed routers and a fixed observer using the WLAN Toolbox™ and trains a neural network (NN) with the simulated data using Deep Learning Toolbox™.
System Description
Assume an indoor space with a number of trusted routers with known MAC addresses, which we will refer to as known routers. Also, assume that unknown routers may enter the observation area, some of which may be router impersonators. The class "Unknown" represents any transmitting device that is not contained in the known set. The following figure shows a scenario where there are three known routers. The observer collects non-high throughput (non-HT) beacon signals from these routers and uses the (legacy) long training field (L-LTF) to identify the RF fingerprint. Transmitted L-LTF signals are the same for all routers that enable the algorithm to avoid any data dependency. Since the routers and the observer are fixed, the RF fingerprints (combination of multipath channel profile and RF impairments) RF1, RF2, and RF3 do not vary in time. Unknown router data is a collection of random RF fingerprints, which are different than the known routers.

The following figure shows a user connected to a router and a mobile hot spot. After training, the observer receives beacon frames and decodes the MAC address. Also, the observer extracts the L-LTF signal and uses this signal to classify the RF fingerprint of the source of the beacon frame. If the MAC address and the RF fingerprint match, as in the case of Router 1, Router 2, and Router 3, then the observer declares the source as a "known" router. If the MAC address of the beacon is not in the database and the RF fingerprint does not match any of the known routers, as in the case of a mobile hot spot, then the observer declares the source as an "unknown" router.
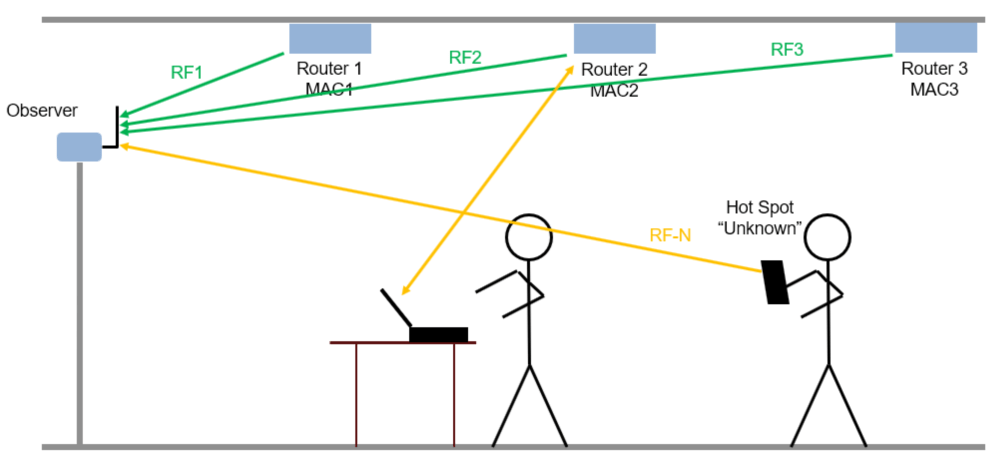
The following figure shows a router impersonator in action. A router impersonator (a.k.a. evil twin) can replicate the MAC address of a known router and transmit beacon frames. Then, the hacker can jam the original router and force the user to connect to the evil twin. The observer receives the beacon frames from the evil twin too and decodes the MAC address. The decoded MAC address matches the MAC address of a known router but the RF fingerprint does not match. The observer declares the source as a router impersonator.

Set System Parameters
Generate a dataset of 5,000 Non-HT WLAN beacon frames for each router. Use MAC addresses as labels for the known routers; the remaining are labeled as "Unknown". A NN is trained to classify the known routers as well as to detect any unknown ones. Split the dataset into training, validation, and test, where the splitting ratios are 80%, 10%, and 10%, respectively. Consider an SNR of 20 dB, working on the 5 GHz band. The number of simulated devices is set to 4 but it can be modified by choosing a different value for numKnownRouters. Set the number of unknown routers more than the known ones to represent in the dataset the variability in the unknown router RF fingerprints.
numKnownRouters = 4; numUnknownRouters = 10; numTotalRouters = numKnownRouters+numUnknownRouters; SNR = 20; % dB channelNumber = 153; % WLAN channel number channelBand = 5; % GHz frameLength = 160; % L-LTF symbol length in samples
By default, this example downloads trained network from https://www.mathworks.com/supportfiles/spc/RFFingerprinting/RFFingerprintingSimulatedData_R2024b.tar. If you do not have an Internet connection, you can download the file manually on a computer that is connected to the Internet and save to the same directory as the current example files.
To run this example quickly, download the pretrained network and generate a small number of frames, for example 10. To train the network on your computer, choose the "Train network now" option (i.e. set trainNow to true). Generating 5000 frames of data takes about 50 minutes on an Intel® Xeon® W-2133 CPU @ 3.6 GHz with 64 GB memory. Training this network takes about 20 seconds with an NVIDIA® GeForce RTX 3080 GPU and about 3 minutes with an Intel® Xeon® W-2133 CPU @ 3.6 GHz.
trainNow =false; if trainNow numTotalFramesPerRouter = 5000; %#ok<UNRCH> else numTotalFramesPerRouter = 10; rfFingerprintingDownloadData('simulated') end
Starting download of data files from: https://www.mathworks.com/supportfiles/spc/RFFingerprinting/RFFingerprintingSimulatedData_R2024b.tar Download and extracting files done
numTrainingFramesPerRouter = numTotalFramesPerRouter*0.8; numValidationFramesPerRouter = numTotalFramesPerRouter*0.1; numTestFramesPerRouter = numTotalFramesPerRouter*0.1;
Generate WLAN Waveforms
Wi-Fi routers that implement 802.11a/g/n/ac protocols transmit beacon frames in the 5 GHz band to broadcast their presence and capabilities using the OFDM non-HT format. The beacon frame consists of two main parts: preamble (SYNC) and payload (DATA). The preamble has two parts: short training and long training. In this example, the payload contains the same bits except the MAC address for each router. The CNN uses the L-LTF part of the preamble as training units. Reusing the L-LTF signal for RF fingerprinting provides an overhead-free fingerprinting solution. Use wlanMACFrameConfig (WLAN Toolbox), wlanMACFrame (WLAN Toolbox), wlanNonHTConfig (WLAN Toolbox), and wlanWaveformGenerator (WLAN Toolbox) functions to generate WLAN beacon frames.
% Create Beacon frame-body configuration object frameBodyConfig = wlanMACManagementConfig; % Create Beacon frame configuration object beaconFrameConfig = wlanMACFrameConfig('FrameType','Beacon',"ManagementConfig",frameBodyConfig); % Generate Beacon frame bits [~,mpduLength] = wlanMACFrame(beaconFrameConfig,'OutputFormat','bits'); % Create a wlanNonHTConfig object, 20 MHz bandwidth and MCS 1 are used nonHTConfig = wlanNonHTConfig('ChannelBandwidth',"CBW20","MCS",1,"PSDULength",mpduLength);
The rfFingerprintingNonHTFrontEnd object performs front-end processing including extracting the L-LTF signal. The object is configured with a channel bandwidth of 20 MHz to process non-HT signals.
rxFrontEnd = rfFingerprintingNonHTFrontEnd('ChannelBandwidth','CBW20'); fc = wlanChannelFrequency(channelNumber,channelBand); fs = wlanSampleRate(nonHTConfig);
Setup Channel and RF Impairments
Pass each frame through a channel with
Rayleigh multipath fading
Radio impairments, such as phase noise, frequency offset and DC offset
AWGN
Rayleigh Multipath and AWGN
The channel passes the signals through a Rayleigh multipath fading channel using the comm.RayleighChannel System object™. Assume a delay profile of [0 1.8 3.4] samples with corresponding average path gains of [0 -2 -10] dB. Since the channel is static, set maximum Doppler shift to zero to make sure that the channel does not change for the same radio. Implement the multipath channel with these settings. Add noise using the awgn function,
multipathChannel = comm.RayleighChannel(... 'SampleRate', fs, ... 'PathDelays', [0 1.8 3.4]/fs, ... 'AveragePathGains', [0 -2 -10], ... 'MaximumDopplerShift', 0);
Radio Impairments
The RF impairments, and their corresponding range of values are:
Phase noise [0.01, 0.3] rms (degrees)
Frequency offset [-4, 4] ppm
DC offset: [-50, -32] dBc
See helperRFImpairments function for more details on RF impairment simulation. This function uses comm.PhaseFrequencyOffset and comm.PhaseNoise System objects.
phaseNoiseRange = [0.01 0.3]; freqOffsetRange = [-4 4]; dcOffsetRange = [-50 -32]; rng(123456) % Fix random generator % Assign random impairments to each simulated radio within the previously defined ranges radioImpairments = repmat(struct('PhaseNoise',0,'DCOffset',0,'FrequencyOffset',0), numTotalRouters,1); for routerIdx = 1:numTotalRouters radioImpairments(routerIdx).PhaseNoise = rand*(phaseNoiseRange(2)-phaseNoiseRange(1)) + phaseNoiseRange(1); radioImpairments(routerIdx).DCOffset = rand*(dcOffsetRange(2)-dcOffsetRange(1)) + dcOffsetRange(1); radioImpairments(routerIdx).FrequencyOffset = fc/1e6*(rand*(freqOffsetRange(2)-freqOffsetRange(1)) + freqOffsetRange(1)); end
Apply Channel Impairments and Generate Data Frames for Training
Apply the RF and channel impairments defined previously. Reset the channel object for each radio to generate an independent channel. Use rfFingerprintingNonHTFrontEnd function to process the received frames. Finally, extract the L-LTF from every transmitted WLAN frame. Split the received L-LTF signals into training, validation and test sets.
% Create variables that will store the training, validation and testing datasets xTrainingFrames = zeros(frameLength,numTrainingFramesPerRouter*numTotalRouters); xValFrames = zeros(frameLength,numValidationFramesPerRouter*numTotalRouters); xTestFrames = zeros(frameLength,numTestFramesPerRouter*numTotalRouters); % Index vectors for train, validation and test data units trainingIndices = 1:numTrainingFramesPerRouter; validationIndices = 1:numValidationFramesPerRouter; testIndices = 1:numTestFramesPerRouter; tic generatedMACAddresses = strings(numTotalRouters,1); rxLLTF = zeros(frameLength,numTotalFramesPerRouter); % Received L-LTF sequences for routerIdx = 1:numTotalRouters % Generate a 12-digit random hexadecimal number as a MAC address for known routers. Set the MAC address of all unknown routers to 'AAAAAAAAAAAA'. if (routerIdx<=numKnownRouters) generatedMACAddresses(routerIdx) = string(dec2hex(bi2de(randi([0 1],12,4)))'); else generatedMACAddresses(routerIdx) = 'AAAAAAAAAAAA'; end elapsedTime = seconds(toc); elapsedTime.Format = 'hh:mm:ss'; fprintf('%s - Generating frames for router %d with MAC address %s\n',elapsedTime,routerIdx,generatedMACAddresses(routerIdx)) % Set MAC address into the wlanFrameConfig object beaconFrameConfig.Address2 = generatedMACAddresses(routerIdx); % Generate beacon frame bits beacon = wlanMACFrame(beaconFrameConfig,'OutputFormat','bits'); txWaveform = wlanWaveformGenerator(beacon,nonHTConfig); txWaveform = helperNormalizeFramePower(txWaveform); % Add zeros to account for channel delays txWaveform = [txWaveform; zeros(160,1)]; %#ok<AGROW> % Reset multipathChannel object to generate a new static channel reset(multipathChannel) frameCount= 0; while frameCount<numTotalFramesPerRouter rxMultipath = multipathChannel(txWaveform); rxImpairment = helperRFImpairments(rxMultipath,radioImpairments(routerIdx),fs); rxSig = awgn(rxImpairment,SNR,0); % Detect the WLAN packet and return the received L-LTF signal using rfFingerprintingNonHTFrontEnd object [valid,~,~,~,~,LLTF] = rxFrontEnd(rxSig); % Save successfully received L-LTF signals if valid frameCount=frameCount+1; rxLLTF(:,frameCount) = LLTF; end if mod(frameCount,500) == 0 elapsedTime = seconds(toc); elapsedTime.Format = 'hh:mm:ss'; fprintf('%s - Generated %d/%d frames\n',elapsedTime,frameCount,numTotalFramesPerRouter) end end rxLLTF = rxLLTF(:,randperm(numTotalFramesPerRouter)); % Split data into training, validation and test xTrainingFrames(:,trainingIndices+(routerIdx-1)*numTrainingFramesPerRouter) = rxLLTF(:,trainingIndices); xValFrames(:,validationIndices+(routerIdx-1)*numValidationFramesPerRouter) = rxLLTF(:,validationIndices + numTrainingFramesPerRouter); xTestFrames(:,testIndices+(routerIdx-1)*numTestFramesPerRouter) = rxLLTF(:,testIndices + numTrainingFramesPerRouter + numValidationFramesPerRouter); end
00:00:00 - Generating frames for router 1 with MAC address 4DA3EE3C8968 00:00:06 - Generating frames for router 2 with MAC address 04BC502F3E35 00:00:06 - Generating frames for router 3 with MAC address A512A15772DA 00:00:07 - Generating frames for router 4 with MAC address 3BB9F27FDFCC 00:00:08 - Generating frames for router 5 with MAC address AAAAAAAAAAAA 00:00:08 - Generating frames for router 6 with MAC address AAAAAAAAAAAA 00:00:09 - Generating frames for router 7 with MAC address AAAAAAAAAAAA 00:00:09 - Generating frames for router 8 with MAC address AAAAAAAAAAAA 00:00:10 - Generating frames for router 9 with MAC address AAAAAAAAAAAA 00:00:10 - Generating frames for router 10 with MAC address AAAAAAAAAAAA 00:00:11 - Generating frames for router 11 with MAC address AAAAAAAAAAAA 00:00:11 - Generating frames for router 12 with MAC address AAAAAAAAAAAA 00:00:12 - Generating frames for router 13 with MAC address AAAAAAAAAAAA 00:00:12 - Generating frames for router 14 with MAC address AAAAAAAAAAAA
% Label received frames. Label the first numKnownRouters with their MAC address. Label the rest with "Unknown”. labels = generatedMACAddresses; labels(generatedMACAddresses == generatedMACAddresses(numTotalRouters)) = "Unknown"; yTrain = repelem(labels,numTrainingFramesPerRouter); yVal = repelem(labels,numValidationFramesPerRouter); yTest = repelem(labels,numTestFramesPerRouter); MACAddresses = unique(yTrain); %#ok<NASGU> % List of unique MAC addresses for prediction
Create Real-Valued Input Matrices
The Deep Learning model only works on real numbers. Thus, I and Q are split into two separate columns. Then, the data is rearranged into a frameLength-by-2-by-1-by-numFrames array, as required by the Deep Learning Toolbox. Additionally, the training set is shuffled, and the label variables are saved as categorical variables.
% Rearrange datasets into a one-column vector xTrainingFrames = xTrainingFrames(:); xValFrames = xValFrames(:); xTestFrames = xTestFrames(:); % Separate between I and Q xTrainingFrames = [real(xTrainingFrames),imag(xTrainingFrames)]; xValFrames = [real(xValFrames),imag(xValFrames)]; xTestFrames = [real(xTestFrames),imag(xTestFrames)]; % Reshape training data into a frameLength x 2 x 1 x numTrainingFramesPerRouter*numTotalRouters matrix xTrainingFrames = permute(reshape(xTrainingFrames,[frameLength,numTrainingFramesPerRouter*numTotalRouters,2,1]),[1 3 4 2]); % Shuffle data vr = randperm(numTotalRouters*numTrainingFramesPerRouter); xTrainingFrames = xTrainingFrames(:,:,:,vr); % Create label vector and shuffle yTrain = categorical(yTrain(vr)); % Reshape validation data into a frameLength x 2 x 1 x numValidationFramesPerRouter*numTotalRouters matrix xValFrames = permute(reshape(xValFrames,[frameLength,numValidationFramesPerRouter*numTotalRouters,2,1]),[1 3 4 2]); % Create label vector yVal = categorical(yVal); % Reshape test dataset into a numTestFramesPerRouter*numTotalRouter matrix xTestFrames = permute(reshape(xTestFrames,[frameLength,numTestFramesPerRouter*numTotalRouters,2,1]),[1 3 4 2]); %#ok<NASGU> % Create label vector yTest = categorical(yTest); %#ok<NASGU>
Train the Neural Network
This example uses a neural network (NN) architecture that consists of two convolutional and three fully connected layers. The intuition behind this design is that the first layer will learn features independently in I and Q. Note that the filter sizes are 1x7. Then, the next layer will use a filter size of 2x7 that will extract features combining I and Q together. Finally, the last three fully connected layers will behave as a classifier using the extracted features in the previous layers [1].
poolSize = [2 1]; strideSize = [2 1]; layers = [ imageInputLayer([frameLength 2 1],'Normalization','none','Name', 'Input Layer') convolution2dLayer([7 1],50,'Padding',[1 0],'Name','CNN1') batchNormalizationLayer('Name','BN1') leakyReluLayer('Name','LeakyReLu1') maxPooling2dLayer(poolSize,'Stride',strideSize,'Name','MaxPool1') convolution2dLayer([7 2],50,'Padding',[1 0],'Name','CNN2') batchNormalizationLayer('Name','BN2') leakyReluLayer('Name','LeakyReLu2') maxPooling2dLayer(poolSize,'Stride',strideSize,'Name','MaxPool2') fullyConnectedLayer(256,'Name','FC1') leakyReluLayer('Name','LeakyReLu3') dropoutLayer(0.5,'Name','DropOut1') fullyConnectedLayer(80,'Name','FC2') leakyReluLayer('Name','LeakyReLu4') dropoutLayer(0.5,'Name','DropOut2') fullyConnectedLayer(numKnownRouters+1,'Name','FC3') softmaxLayer('Name','SoftMax') ]
layers =
17×1 Layer array with layers:
1 'Input Layer' Image Input 160×2×1 images
2 'CNN1' 2-D Convolution 50 7×1 convolutions with stride [1 1] and padding [1 1 0 0]
3 'BN1' Batch Normalization Batch normalization
4 'LeakyReLu1' Leaky ReLU Leaky ReLU with scale 0.01
5 'MaxPool1' 2-D Max Pooling 2×1 max pooling with stride [2 1] and padding [0 0 0 0]
6 'CNN2' 2-D Convolution 50 7×2 convolutions with stride [1 1] and padding [1 1 0 0]
7 'BN2' Batch Normalization Batch normalization
8 'LeakyReLu2' Leaky ReLU Leaky ReLU with scale 0.01
9 'MaxPool2' 2-D Max Pooling 2×1 max pooling with stride [2 1] and padding [0 0 0 0]
10 'FC1' Fully Connected 256 fully connected layer
11 'LeakyReLu3' Leaky ReLU Leaky ReLU with scale 0.01
12 'DropOut1' Dropout 50% dropout
13 'FC2' Fully Connected 80 fully connected layer
14 'LeakyReLu4' Leaky ReLU Leaky ReLU with scale 0.01
15 'DropOut2' Dropout 50% dropout
16 'FC3' Fully Connected 5 fully connected layer
17 'SoftMax' Softmax softmax
Configure the training options to use the ADAM optimizer with a mini-batch size of 512. By default, 'ExecutionEnvironment' is set to 'auto', which uses a GPU for training if one is available. Otherwise, trainnet (Deep Learning Toolbox) uses a CPU for training. To explicitly set the execution environment, set 'ExecutionEnvironment' to one of 'cpu', 'gpu', 'multi-gpu', or 'parallel'.
if trainNow miniBatchSize = 512; %#ok<UNRCH> iterPerEpoch = floor(numTrainingFramesPerRouter*numTotalRouters/miniBatchSize); % Training options options = trainingOptions('adam', ... 'MaxEpochs', 5, ... 'ValidationData', {xValFrames,yVal}, ... 'ValidationFrequency', iterPerEpoch, ... 'Verbose', false, ... 'InitialLearnRate', 0.001, ... 'LearnRateSchedule', 'piecewise', ... 'LearnRateDropFactor', 0.5, ... 'LearnRateDropPeriod', 2, ... 'MiniBatchSize', miniBatchSize, ... 'Plots', 'training-progress', ... 'Shuffle', 'every-epoch', ... 'Metrics', "accuracy", ... 'ExecutionEnvironment', "auto"); % Train the network [simNet,info] = trainnet(xTrainingFrames,yTrain,layers,"crossentropy",options); else % Load trained network (simNet), testing dataset (xTestFrames and yTest) and the used MACAddresses (generated MAC addresses) load('rfFingerprintingSimulatedDataTrainedNN_R2024b.mat','generatedMACAddresses','simNet','xTestFrames','yTest','MACAddresses'); end
Classify test frames and calculate the final accuracy of the neural network.
% Obtain predicted classes for xTestFrames yTestPred = predict(simNet,xTestFrames); yLabel = scores2label(yTestPred,MACAddresses'); % Calculate test accuracy testAccuracy = mean(yTest == yLabel); disp("Test accuracy: " + testAccuracy*100 + "%")
Test accuracy: 100%
Plot the confusion matrix for the test frames. As mentioned before, perfect classification accuracy is achieved with the synthetic dataset.
figure cm = confusionchart(yTest,yLabel); cm.Title = 'Confusion Matrix for Test Data'; cm.RowSummary = 'row-normalized';

Detect Router Impersonator
Generate beacon frames with the known MAC addresses and one unknown MAC address. Generate a new set of RF impairments and multipath channel. Since the impairments are all new, the RF fingerprint for these frames should be classified as "Unknown". The frames with known MAC addresses represent router impersonators while the frames with unknown MAC addresses are simply unknown routers.
framesPerRouter = 4; knownMACAddresses = generatedMACAddresses(1:numKnownRouters); % Assign random impairments to each simulated radio within the previously % defined ranges for routerIdx = 1:numTotalRouters radioImpairments(routerIdx).PhaseNoise = rand*( phaseNoiseRange(2)-phaseNoiseRange(1) ) + phaseNoiseRange(1); radioImpairments(routerIdx).DCOffset = rand*( dcOffsetRange(2)-dcOffsetRange(1) ) + dcOffsetRange(1); radioImpairments(routerIdx).FrequencyOffset = fc/1e6*(rand*( freqOffsetRange(2)-freqOffsetRange(1) ) + freqOffsetRange(1)); end % Reset multipathChannel object to generate a new static channel reset(multipathChannel) % Run for all known routers and one unknown for macIndex = 1:(numKnownRouters+1) beaconFrameConfig.Address2 = generatedMACAddresses(macIndex); % Generate Beacon frame bits beacon = wlanMACFrame(beaconFrameConfig,'OutputFormat','bits'); txWaveform = wlanWaveformGenerator(beacon,nonHTConfig); txWaveform = helperNormalizeFramePower(txWaveform); % Add zeros to account for channel delays txWaveform = [txWaveform; zeros(160,1)]; %#ok<AGROW> % Create an unseen multipath channel. In other words, create an unseen % RF fingerprint. reset(multipathChannel) frameCount= 0; while frameCount<framesPerRouter rxMultipath = multipathChannel(txWaveform); rxImpairment = helperRFImpairments(rxMultipath,radioImpairments(routerIdx),fs); rxSig = awgn(rxImpairment,SNR,0); % Detect the WLAN packet and return the received L-LTF signal using rfFingerprintingNonHTFrontEnd object [payloadFull,cfgNonHT,rxNonHTData,chanEst,noiseVar,LLTF] = rxFrontEnd(rxSig); if payloadFull frameCount = frameCount+1; recBits = wlanNonHTDataRecover(rxNonHTData,chanEst,noiseVar,cfgNonHT,'EqualizationMethod','ZF'); % Decode and evaluate recovered bits mpduCfg = wlanMPDUDecode(recBits,cfgNonHT); % Separate I and Q and reshape for neural network LLTF= [real(LLTF),imag(LLTF)]; LLTF = permute(reshape(LLTF,frameLength,[],2,1),[1 3 4 2]); ypred = predict(simNet,LLTF); yLabel = scores2label(ypred,categories(yTrain)); if sum(contains(knownMACAddresses,mpduCfg.Address2)) ~= 0 if categorical(convertCharsToStrings(mpduCfg.Address2))~=yLabel disp(strcat("MAC Address ",mpduCfg.Address2," is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED")) else disp(strcat("MAC Address ",mpduCfg.Address2," is known, fingerprint match")) end else disp(strcat("MAC Address ",mpduCfg.Address2," is not recognized, unknown device")) end end % Reset multipathChannel object to generate a new static channel reset(multipathChannel) end end
MAC Address 4DA3EE3C8968 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 4DA3EE3C8968 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 4DA3EE3C8968 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 4DA3EE3C8968 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 6AD7E138CB4B is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 6AD7E138CB4B is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 6AD7E138CB4B is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 6AD7E138CB4B is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address A98C47937892 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address A98C47937892 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address A98C47937892 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address A98C47937892 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 4767DFA4E601 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 4767DFA4E601 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 4767DFA4E601 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED MAC Address 4767DFA4E601 is known, fingerprint mismatch, ROUTER IMPERSONATOR DETECTED
MAC Address AAAAAAAAAAAA is not recognized, unknown device MAC Address AAAAAAAAAAAA is not recognized, unknown device MAC Address AAAAAAAAAAAA is not recognized, unknown device MAC Address AAAAAAAAAAAA is not recognized, unknown device
Further Exploration
You can test the system under different channel and RF impairments by modifying the
Multipath profile (
PathDelaysandAveragePathGainsproperties of Rayleigh channel object),Channel noise level (SNR input of
awgnfunction),RF impairments (
phaseNoiseRange,freqOffsetRange, anddcOffsetRangevariables).
You can also modify the neural network structure by changing
Convolutional layer parameters (filter size, number of filters, padding),
Number of fully connected layers,
Number of convolutional layers.
Appendix: Helper Functions
function [impairedSig] = helperRFImpairments(sig,radioImpairments,fs) % helperRFImpairments Apply RF impairments % IMPAIREDSIG = helperRFImpairments(SIG,RADIOIMPAIRMENTS, FS) returns signal % SIG after applying the impairments defined by RADIOIMPAIRMENTS % structure at the sample rate FS. % Apply frequency offset fOff = comm.PhaseFrequencyOffset('FrequencyOffset',radioImpairments.FrequencyOffset,'SampleRate',fs); % Apply phase noise phaseNoise = helperGetPhaseNoise(radioImpairments); phNoise = comm.PhaseNoise('Level',phaseNoise,'FrequencyOffset',abs(radioImpairments.FrequencyOffset)); impFOff = fOff(sig); impPhNoise = phNoise(impFOff); % Apply DC offset impairedSig = impPhNoise + 10^(radioImpairments.DCOffset/10); end function [phaseNoise] = helperGetPhaseNoise(radioImpairments) % helperGetPhaseNoise Get phase noise value load('Mrms.mat','Mrms','MyI','xI'); [~, iRms] = min(abs(radioImpairments.PhaseNoise - Mrms)); [~, iFreqOffset] = min(abs(xI - abs(radioImpairments.FrequencyOffset))); phaseNoise = -abs(MyI(iRms,iFreqOffset)); end
Selected Bibliography
[1] K. Sankhe, M. Belgiovine, F. Zhou, S. Riyaz, S. Ioannidis and K. Chowdhury, "ORACLE: Optimized Radio clAssification through Convolutional neuraL nEtworks," IEEE INFOCOM 2019 - IEEE Conference on Computer Communications, Paris, France, 2019, pp. 370-378.
See Also
Topics
- Deep Learning in MATLAB (Deep Learning Toolbox)